Why Single Sign On is Important?
With the web 2.0, online authentication has evolved. Social networking platforms provide unique opportunity for online businesses to bring their products up close to the customers in their virtual lives. User behaviour on these sites gives the businesses a unique view on each of their customer’s personal preferences.
With the web 2.0, there are new and growing algorithms to understand the user behaviour on different social networks. These are then used by the platforms such as Facebook, twitter and google to post adverts of companies which the user would have a better chance of logging into using the single sign on capability for authentication. With the virtual social circles other related users are also notified regarding your new customer. Google android apps are a prime example where shopping for a new app the user’s friends can know what the user has shopped or preferred to use.
All this is capable by the new authentication mechanisms provided on the internet. The single sign on feature where the users can log into another software system having authenticated at one of the social login’s or any other software systems which have used the OAuth servers for authenticating their users.
The authentication online now is growing more to be independent of the websites that the user’s are logging onto. This helps each of the ISV’s to reduce the number of steps required by each of their users to use the ISV’s product.
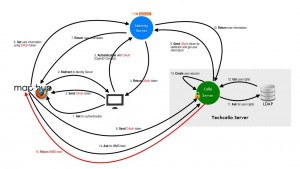 A B2B business model, where an ISV is more focussed to getting a business of an already setup company, should have the capability to use the credentials of the companies users with the already in place authenticating system of each of the company. This is a developing pain point for ISV’s which had an on premise model of the product where internal login would be possible.
A B2B business model, where an ISV is more focussed to getting a business of an already setup company, should have the capability to use the credentials of the companies users with the already in place authenticating system of each of the company. This is a developing pain point for ISV’s which had an on premise model of the product where internal login would be possible.
With more and more businesses moving onto the cloud, it is cheaper for ISV’s to serve their product on the cloud in the SaaS based model, reducing the installation charges for each of the customer and supporting them live. This though raises newer challenges, in authentication and security, since all the different tenant’s ie the customer’s and their end users have to be authenticated separately and provided their own provision.
This is answered by having OAuth. Depending on the tenant/company the user can be directed to his own authentication provider, once authenticated the system sends a token to the Oauth server. The token is matched to user’s authorization parameters, thus authenticating the user without getting the credentials.



